Best Practices for Securing Your Network from Ransomware
66% of organizations were hit by ransomware in the last year.
Is your endpoint protection solution optimally configured to protect against these devastating attacks?
Read this guide to:
- Learn how ransomware attacks work
- Discover the six endpoint-protection best practices all organizations should deploy
- Get top security tips to help keep ransomware at bay
Ransomware Attacks Are Increasing in Volume and Severity
66% of organizations were hit by ransomware last year, up from 37% in 2020. This is a 78% year-over-year increase, demonstrating that adversaries have become considerably more capable at executing attacks at scale than ever before. The surge in ransomware likely also reflects the growing success of the ransomware-as-a- service model, which extends the reach of ransomware by reducing the skill level required to deploy an attack.
How Ransomware Attacks Work
To understand how to protect against ransomware attacks, we first need to examine how they work. A typical targeted ransomware attack looks like this:
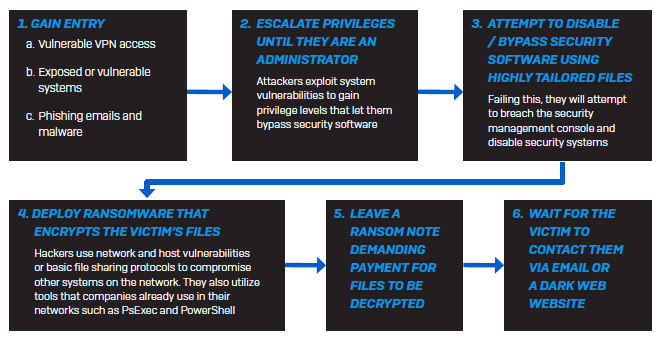
Modern ransomware attacks often use legitimate IT and end-user tools such as a VPN or Remote Desktop Protocol (RDP) to gain access. These tools are used by authorized staff as part of their jobs, making initial detection of modern ransomware attacks difficult. The root of the problem is that there’s too much implicit trust in the use of these tools — anyone who can access a VPN or RDP is assumed to be trusted, a practice which has proven time and time again to be unwise.

