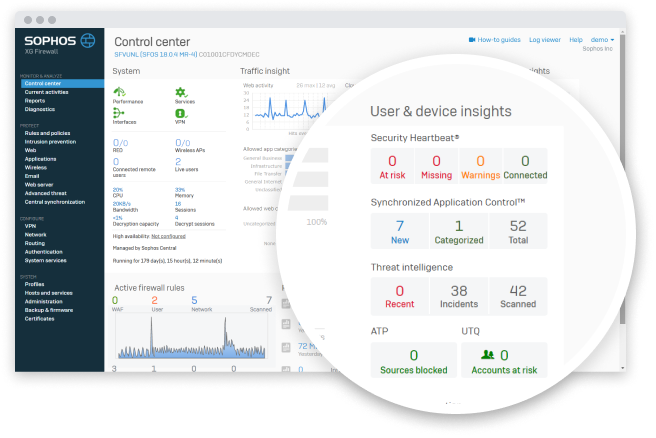
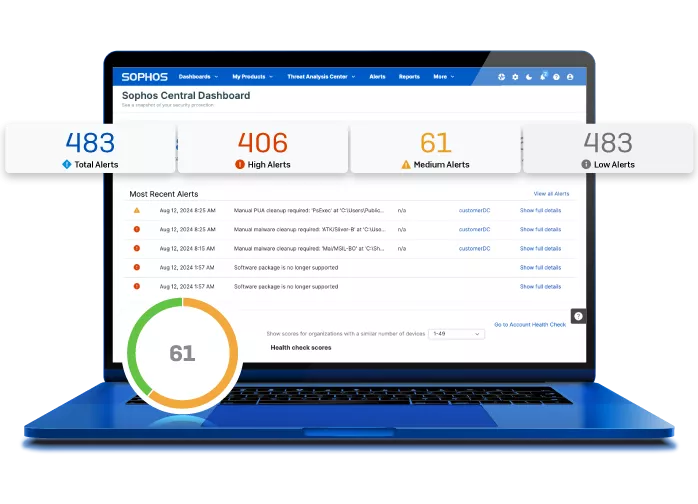
Power-Up Security Teams
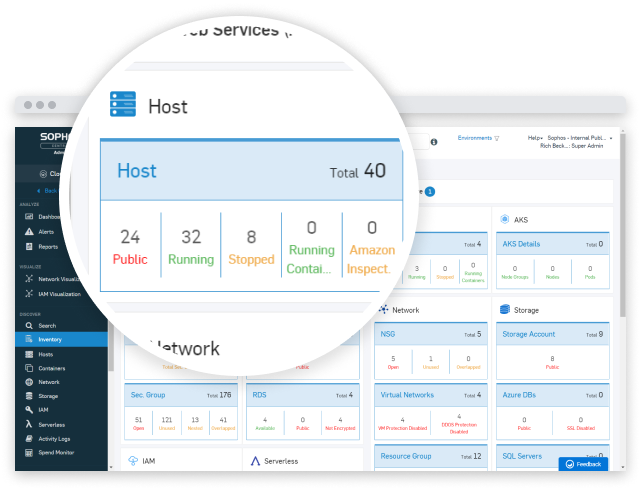
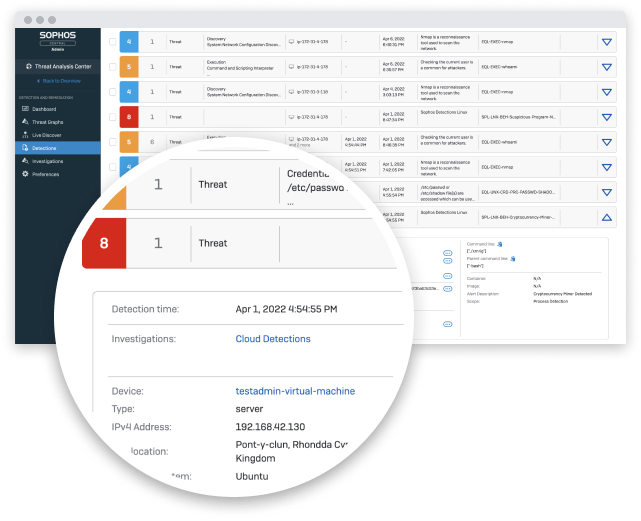
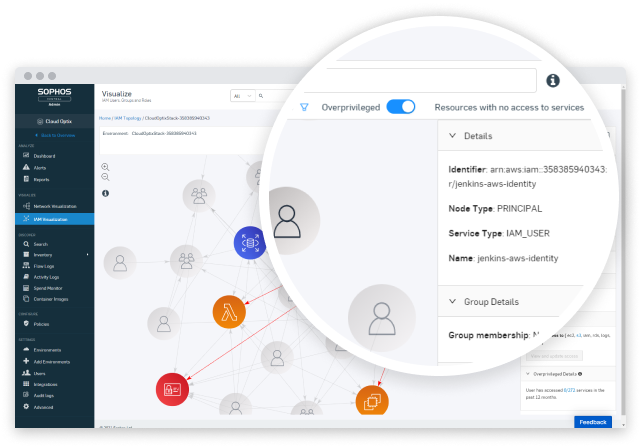
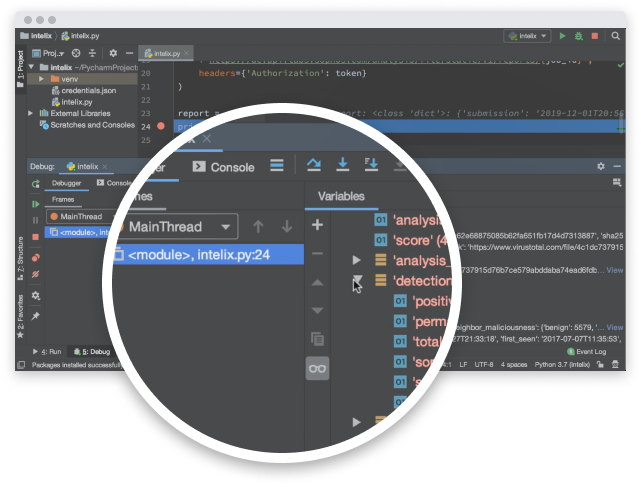
Boost efficiency with a single integrated cloud security platform. Sophos Cloud Native Security unifies security tools across workloads, cloud environments, and entitlements management. Integrated with SIEM, collaboration, workflow, and DevOps tools to increase agility across an organization.